-
-
October 1, 2020 at 3:10 pm
user deleted
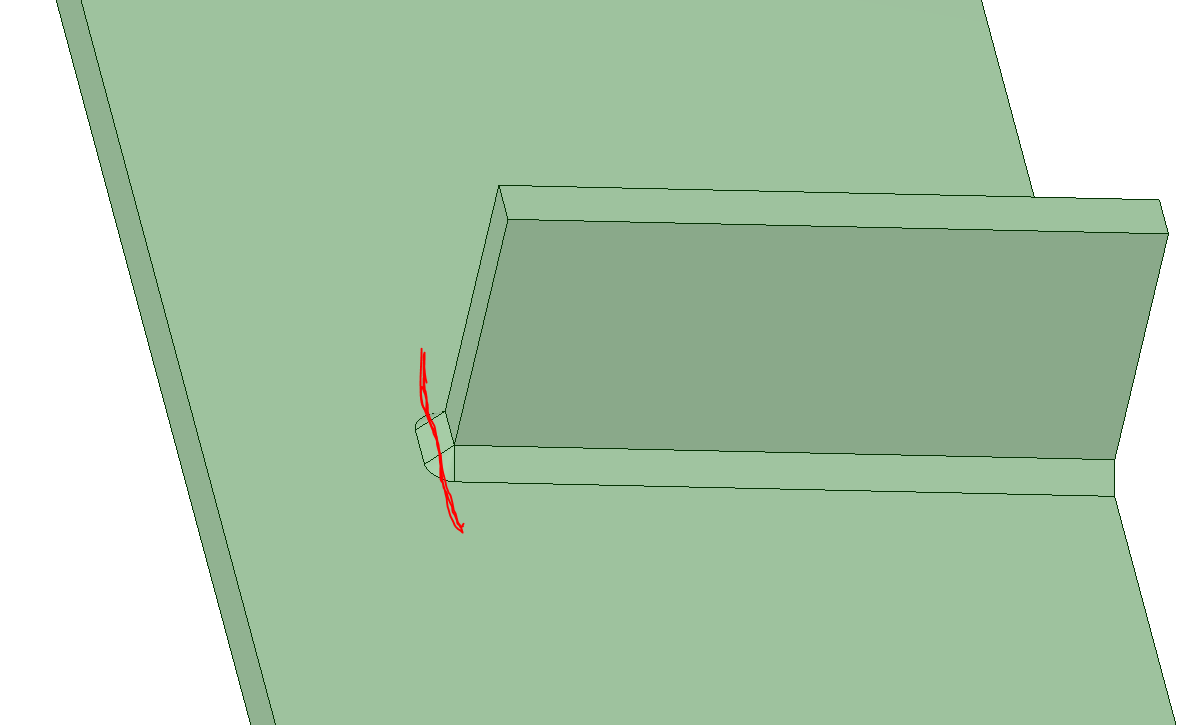
SubscriberHello, dear members of the forum! Can you please tell me, except how through creating a cut in the geometry it is impossible to model a through crack? I mean 2 approaches: creating a rectangular cut-through in geometry with subsequent implantation of a semi-elliptical crack at the ends, or creating a cut-through with sharp ends at the vertices and then applying a premeshed crack. And will these approaches be correct?
October 28, 2020 at 10:04 pmDavid Weed
Ansys EmployeeHello,nWith our current tools, the crack front (the nodes along the edge which comprise the initial crack tip) needs to be contiguous. If modeling a through-crack, adhering to this requirement doesn't seem feasible. However, if you're performing crack growth (via SMART, XFEM, or manually growing the crack yourself) you could use either a semi-elliptical or premeshed crack as an initial surface crack and then as the crack grows it could eventually become a through-crack. Or, if you want to model the initial crack in such a way that it is very close to the final boundary or outer wall and then calculate what is the critical K or J value that will cause the crack to penetrate that wall, then a premeshed crack could work in this case, since you're starting with a contiguous crack front. Please let me know if I'm understanding the problem correctly and I should be able to provide further guidance. Thank you.nViewing 1 reply thread- The topic ‘Through_crack_modeling_approaches’ is closed to new replies.
Innovation SpaceTrending discussionsTop Contributors-
4683
-
1565
-
1386
-
1242
-
1021
Top Rated Tags© 2025 Copyright ANSYS, Inc. All rights reserved.
Ansys does not support the usage of unauthorized Ansys software. Please visit www.ansys.com to obtain an official distribution.
-
The Ansys Learning Forum is a public forum. You are prohibited from providing (i) information that is confidential to You, your employer, or any third party, (ii) Personal Data or individually identifiable health information, (iii) any information that is U.S. Government Classified, Controlled Unclassified Information, International Traffic in Arms Regulators (ITAR) or Export Administration Regulators (EAR) controlled or otherwise have been determined by the United States Government or by a foreign government to require protection against unauthorized disclosure for reasons of national security, or (iv) topics or information restricted by the People's Republic of China data protection and privacy laws.